Table of Contents
Introduction
Enterprises today are operating in an environment where the traditional security perimeter no longer exists. With the widespread adoption of cloud services, hybrid work models, and globally distributed teams, data and applications are no longer confined to centralized corporate networks. Employees, contractors, and partners now access resources from multiple devices and locations, making perimeter-based defenses inadequate.
At the same time, attackers are exploiting vulnerabilities in legacy virtual private networks (VPNs) and capitalizing on insider threats. VPNs, which were once the default tool for remote access, provide broad network connectivity that often grants more access than necessary, increasing risks if credentials are compromised.
This has led to a major shift in enterprise security models, with Zero Trust Network Access (ZTNA) emerging as the standard for secure connectivity. Unlike traditional methods, ZTNA focuses on verifying every access request, limiting permissions, and continuously monitoring behavior, ensuring that trust is never assumed.
What Is ZTNA?
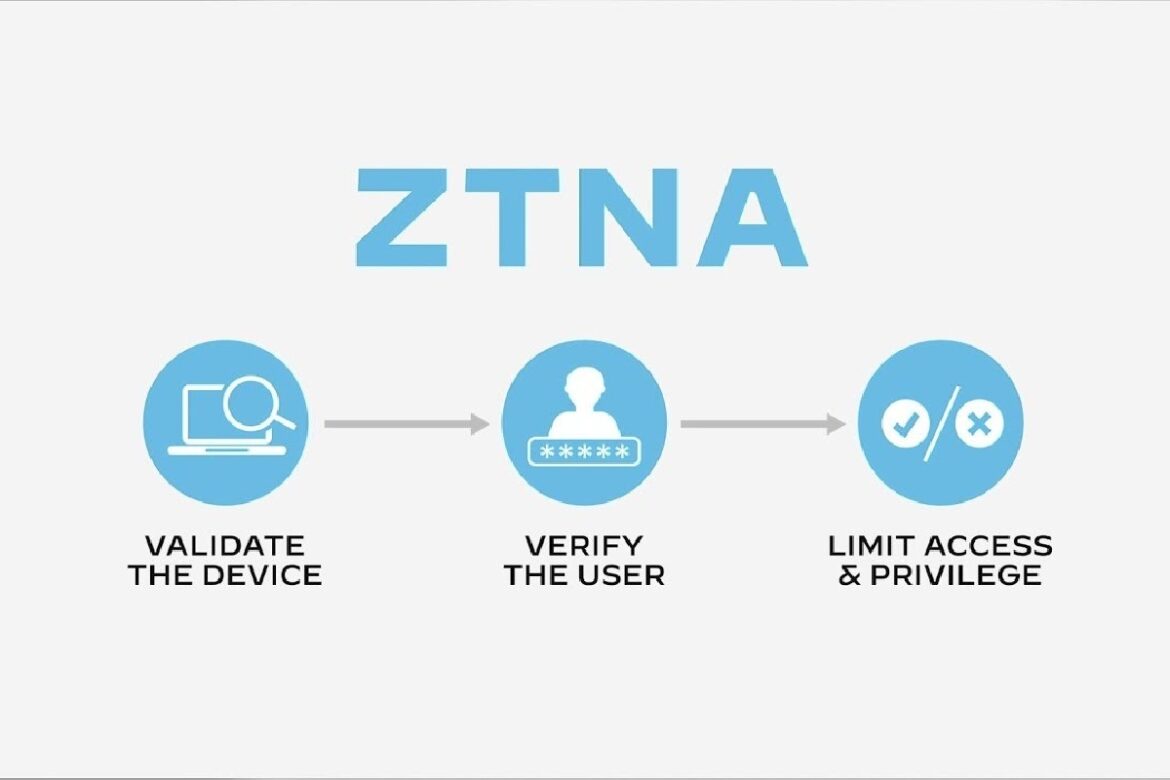
Zero Trust Network Access, or ZTNA, is a modern security approach designed to control access to applications and resources based on strict verification. In simple terms, ZTNA ensures that no user or device is trusted by default, regardless of whether they are inside or outside the corporate network.
The guiding principle of ZTNA is “Never trust, always verify.” Every access request is validated against identity, device health, location, and context before permission is granted. Unlike VPNs that connect users to an entire network, ZTNA restricts access to only the specific applications or resources the user is authorized to use.
This approach reduces the risk of lateral movement within a network and ensures better alignment with cloud-first strategies. ZTNA explained: How it improves network security is not only about controlling access but also about enforcing real-time, adaptive policies that evolve with user behavior and emerging threats.
How ZTNA Works
ZTNA operates by verifying users and devices before establishing a connection to an application. Instead of providing broad access, it enforces identity-first authentication, where policies determine what level of access is appropriate.
These policies are context-aware, meaning they take into account details such as device posture, user role, geographic location, and even the sensitivity of the application being accessed. This granular control ensures that even if an attacker compromises credentials, the damage is limited.
ZTNA also leverages application-level segmentation, meaning that users are only connected to the resources they need and nothing more. This not only enhances security but also streamlines user access, providing a more efficient and seamless experience.
Core Components of ZTNA
The foundation of ZTNA lies in strong identity and access management. Multifactor authentication, integration with identity providers, and continuous verification of user sessions ensure that access is never static.
ZTNA enforces least-privilege access, granting only the minimum level of permissions required. This reduces exposure and limits the impact of compromised accounts. Continuous monitoring allows organizations to adapt policies in real time, responding to abnormal activity as it occurs.
Another key feature is encrypted connections. Secure brokers act as intermediaries between users and applications, ensuring that traffic is protected end-to-end while maintaining visibility into access behavior.
Benefits of Adopting ZTNA
Organizations adopting ZTNA gain multiple security and business benefits. The most notable is a reduced attack surface. Since users are only granted access to specific applications, the risk of lateral movement across networks is minimized.
ZTNA also enhances the security of hybrid and remote workforces by providing secure, application-specific access rather than broad network entry. This simplifies IT management, as policies can be applied and enforced centrally.
From a user perspective, ZTNA provides a smoother experience compared to traditional VPNs, eliminating the need for always-on connectivity and reducing latency when accessing cloud applications.
ZTNA in Real-World Applications
In finance, ZTNA is being used to secure sensitive digital transactions and ensure compliance with strict data protection regulations. It provides granular access control that helps reduce fraud risks while safeguarding customer data.
Healthcare organizations are adopting ZTNA to protect patient data and secure telehealth services. With connected medical systems and remote care increasing, this granular security is essential.
In manufacturing, ZTNA is helping to secure industrial IoT and operational technology systems, ensuring that external contractors or vendors only have access to the systems they need.
Educational institutions are using ZTNA to provide secure access for students and faculty, enabling remote learning while protecting critical research and institutional data.
For a broader understanding of Zero Trust frameworks, the National Institute of Standards and Technology (NIST) has published guidelines that help organizations adopt Zero Trust approaches effectively.
Challenges in ZTNA Adoption
Despite its benefits, adopting ZTNA comes with challenges. Integrating it into existing IT and OT infrastructures can be complex, especially for organizations with legacy systems that were not designed for modern access controls.
User adoption can also present difficulties, as employees may initially find the transition from VPNs to ZTNA disruptive. Proper training and communication are essential to smooth this shift.
There is also the risk of vendor lock-in, as some ZTNA providers offer solutions that may not integrate easily with other tools. Enterprises must carefully evaluate scalability and interoperability before committing.
Best Practices for Implementing ZTNA
Successful ZTNA deployment begins with a thorough security gap assessment to identify critical applications and resources that need immediate protection. Rolling out ZTNA for high-value applications first ensures a focused and impactful start.
Integration with identity providers and multifactor authentication strengthens authentication mechanisms, making it harder for attackers to exploit compromised credentials. Policies should be continuously monitored and refined to adapt to evolving threats.
The Cybersecurity and Infrastructure Security Agency (CISA) provides practical guidance for organizations transitioning to Zero Trust architectures, including ZTNA adoption strategies.
ZTNA vs. VPN: Why Enterprises Are Moving On
While VPNs have long been the default for remote access, they come with significant drawbacks. VPNs often provide broad network-level access, meaning a single compromised account can potentially expose an entire network.
ZTNA, by contrast, restricts access at the application level. It provides better scalability for multi-cloud and hybrid environments, aligning with Zero Trust principles and modern compliance requirements. This makes ZTNA the preferred choice for organizations looking to balance security, usability, and agility.
For more insights into Zero Trust adoption trends, the Gartner research hub frequently analyzes enterprise strategies around ZTNA and related technologies.
The Future of ZTNA in Secure Access
The future of ZTNA lies in the integration of artificial intelligence and machine learning, enabling adaptive access controls that learn from user behavior. This evolution will make security more predictive and proactive.
ZTNA will also play a larger role in Secure Access Service Edge (SASE) frameworks, combining networking and security into unified cloud-based platforms. As enterprises increasingly adopt multi-cloud environments, ZTNA will serve as a foundation for broader Zero Trust strategies.
Over time, adoption is expected to expand beyond large enterprises, with small and mid-sized businesses embracing ZTNA as a cost-effective security solution.
Conclusion
ZTNA is rapidly becoming an essential element of enterprise security. By eliminating implicit trust and focusing on continuous verification, it provides the protection needed in cloud-first, hybrid, and highly dynamic environments.
It is not just a security strategy but also a business enabler, simplifying IT management, improving user experiences, and reducing risks. For organizations aiming to future-proof their defenses, adopting ZTNA is no longer optional; it is a critical step toward resilience and growth.
FAQs
How does ZTNA differ from a traditional VPN?
VPNs provide broad network access, while ZTNA grants application-level access based on strict policies. This minimizes risks if credentials are compromised.
Is ZTNA suitable for small and mid-sized businesses?
Yes. While initially adopted by large enterprises, ZTNA solutions are increasingly scalable and cost-effective, making them accessible to SMBs.
Can ZTNA fully protect against insider threats?
ZTNA significantly reduces risks by limiting access and continuously monitoring behavior, but it should be combined with other security measures like monitoring tools and employee training for comprehensive protection.